SecureCRT includes a built-in TFTP server that can be used as a file transfer target/source for a TFTP client on another device. The device where the TFTP client is running must have a network path to the machine where SecureCRT is running (UDP, port 69).
To manually start or stop the TFTP server in SecureCRT, open the Transfer menu and select the Start TFTP Server menu item. If the TFTP server is already running, the label of the menu item will display Stop TFTP Server.
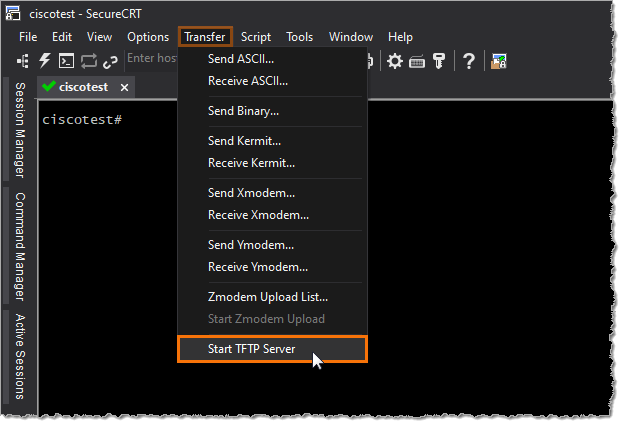
Additionally, SecureCRT's TFTP server can be configured to start automatically in SecureCRT's Global Options / Terminal / TFTP Server category.
To automatically start the TFTP server when the SecureCRT application is launched, enable the Start TFTP server when option and then select the SecureCRT starts option.
To automatically start the TFTP server whenever any session is used to make a connection, enable Start TFTP server when option and then select Any session connects.
Note: Regardless of the mechanism used to start the TFTP server, the TFTP server will remain running until either:
Note for SecureCRT on macOS
SecureCRT on the macOS platform installs a binding helper to allow the TFTP server to bind to port 69, which is "privileged" in macOS. If SecureCRT is not installed properly, SecureCRT's TFTP binding helper may not be able to successfully bind to port 69. To correctly install SecureCRT, open the DMG and drag the SecureCRT application from the DMG to the Applications folder in the Finder app on your Mac. Always launch the SecureCRT app directly from the Applications folder, rather than launching SecureCRT directly from the mounted DMG.
Note for SecureCRT on Ubuntu
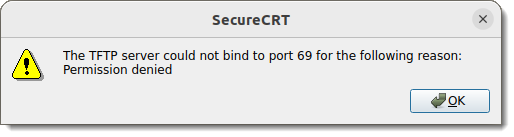
On Ubuntu platforms, SecureCRT won't be able to bind to port 69 by default. This is because Ubuntu considers all ports below 1024 to be "privileged", and individuals won't typically be running SecureCRT as the root user. Because of this, if you try to start the TFTP server in SecureCRT on Ubuntu, you'll see the following error message:
To configure Ubuntu to allow SecureCRT to listen on a privileged port (such as the TFTP port, 69):
sudo setcap 'cap_net_bind_service=+ep' `which SecureCRT`
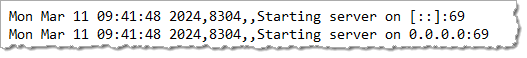
When the TFTP server is started, SecureCRT's status bar will report, "TFTP server is ready," and will include in parenthesis the first non-loopback network interface provided by the operating system on which SecureCRT is running.
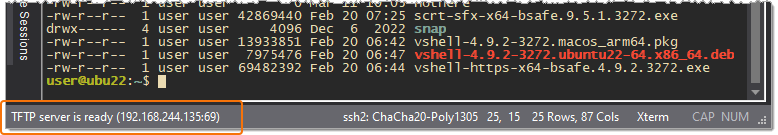
Note: Because of limited space available in the status bar, only the first non-loopback network interface is displayed. However, the TFTP server will listen on all available network interfaces on the machine where SecureCRT is running. This can be verified by opening a local shell console and running the command appropriate for the operating system on which SecureCRT is running. For example:
Windows
Powershell:
gps -ID (Get-NetUDPEndpoint -LocalPort 69).OwningProcess | ft -Property ProcessName,Id,PathCMD:
netstat -an | findstr ":69"macOS
lsof -i UDP | grep -E ":69|tftp"Ubuntu
sudo lsof -i UDP | grep -E ":69|tftp"
If you don't know the IP addresses of the network interfaces available on your machine where you're running SecureCRT, the following commands may be helpful when run in a Local Shell connection in SecureCRT:
Windows
Powershell:
gip | ? {$_.NetAdapter.Status -ne "Disconnected"} | ft -Property IPv4Address,InterfaceAliasCMD:
ipconfig /all | findstr "IPv4"macOS
ifconfig | grep -o -E "inet \S+"Ubuntu
ip a | grep -o -E "inet\s+[^/]+"
TFTP stands for the "Trivial File Transfer Protocol" and it is trivial, indeed. The TFTP protocol does not provide any user authentication, access control, or encryption between the TFTP client and the TFTP server.
To help mitigate the inherent lack of security associated with the TFTP protocol, SecureCRT provides the following features:
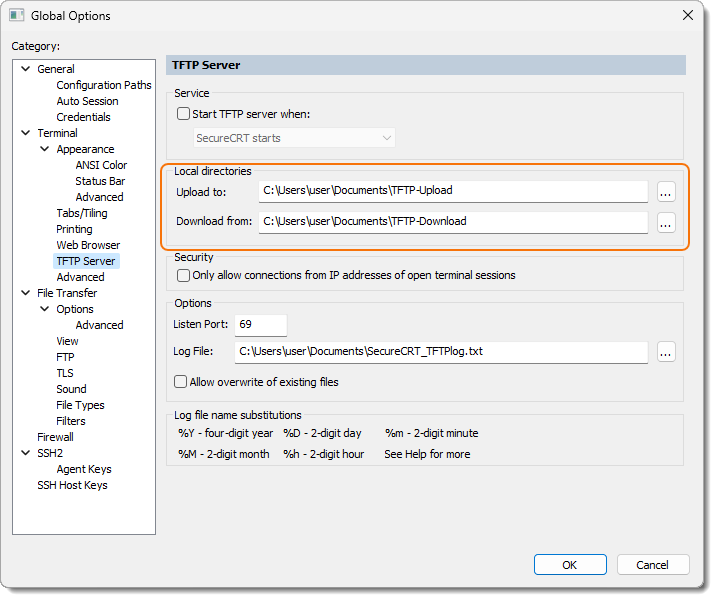
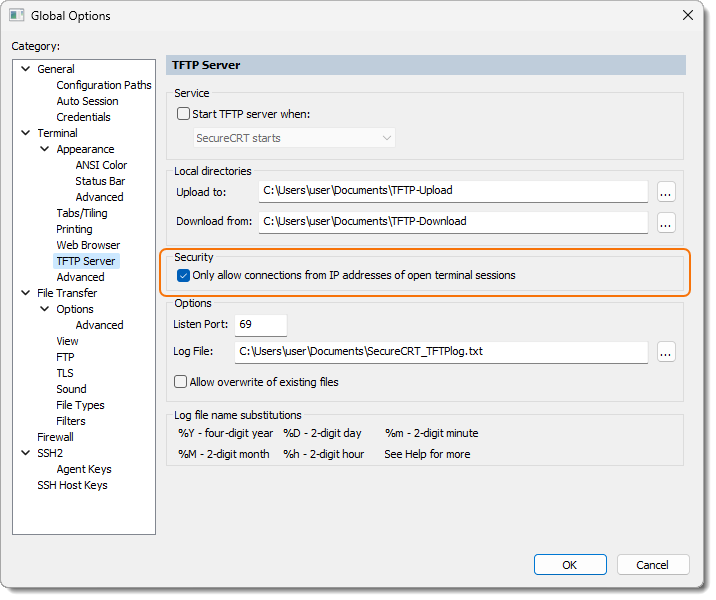
Enable the Only allow connections from IP addresses of open terminal sessions. Disable this option only if you're unable to control which network interface your TFTP client uses to attempt to establish the TFTP connection, and the TFTP client attempt times out.
Note: If a TFTP client connection is attempted from an IP address which does not match the IP addresses of any open terminal sessions in SecureCRT, the TFTP log file (if enabled) will display an error message. For example, "Request received from invalid IP address: nnn.nnn.nnn.nnn."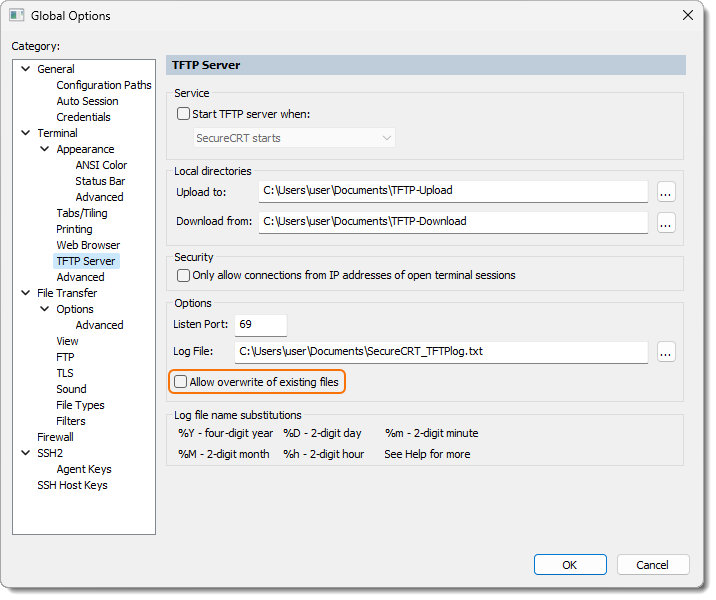
Enable the Allow overwrite of existing files option only if (a) you have enabled the Only allow connections from IP addresses of open terminal sessions option, or (b) you are operating SecureCRT within a secured network environment where you are certain that no TFTP attacks are possible.
VanDyke Software uses cookies to give you the best online experience. Before continuing to use this site, please confirm that you agree to our use of cookies. Please see our Cookie Usage for details.
Here you can control cookies using the checkboxes below. Some cookies are essential for the use of our website and cannot be disabled. Others provide a convenience to the user and, if disabled, may reduce the ease of use of our site. Finally, some cookies provide anonymous analytic tracking data that help us provide the user with a richer browsing experience. You can elect to disable these cookies as well.