With today's increasingly mobile and distributed workforce, providing remote access to travelers and teleworkers is no longer a "nice to have" option. In many corporations, remote access to business applications has become mission critical. At the same time, Internet access is now cheap, fast, and readily available. Leveraging the Internet to extend the local area network (LAN), provide real-time communications, and immediate file transfer and sharing is a scalable, cost-effective solution for corporate network remote access.
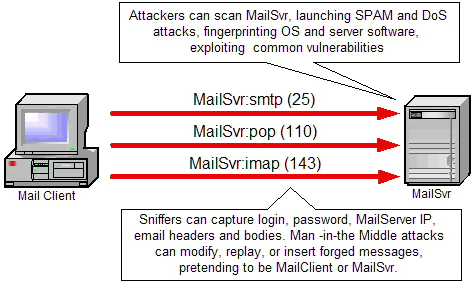
However, Internet-based remote access also adds significant risk. Sensitive data can be intercepted, modified, or replayed anywhere between remote workers and the corporate firewall. Broadcast access technologies like cable and wireless are especially vulnerable. Whenever a computer is connected to the Internet, it becomes a potential target for intruders. "Always on" broadband greatly increases this exposure by giving intruders a fixed target to attack repeatedly over time. Unless appropriate measures are taken, allowing remote access over the Internet can compromise usernames, passwords, proprietary data, traveler laptops, teleworker PCs — even the corporate network itself.
Secure Shell (often referred to as SSH) can help to neutralize these threats and make the most of secure Internet-based remote access. This standard protocol employs authentication and encryption to ensure the privacy and integrity of data exchanged between clients and servers. To learn more about Secure Shell protocols, authentication methods, and cryptography, refer to our Secure Shell Overview.
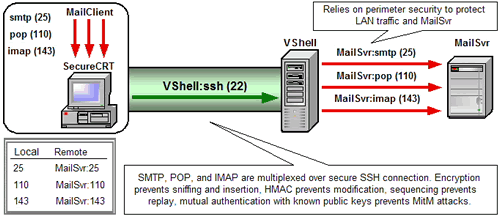
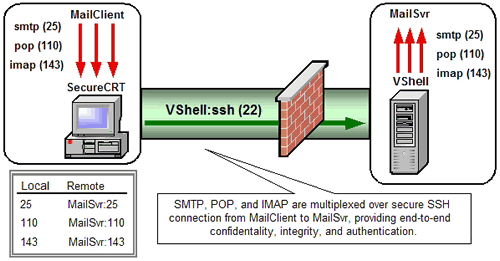
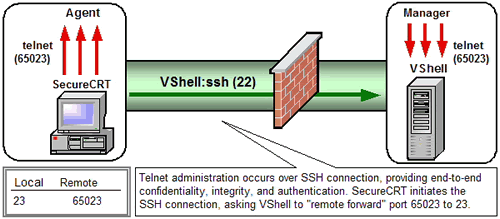
Secure Shell can tunnel data from any TCP application with a predefined listening port In TCP/IP networks, a port number identifies what protocol is listened for. Port 80, for example, is used for HTTP traffic. . Commonly known as "port forwarding", Secure Shell tunneling makes it easy to secure applications that would otherwise send unprotected traffic across public networks. Application messages relayed from one end of a Secure Shell connection to the other are protected by the cryptographic measures negotiated for that connection. Because several applications can be multiplexed over a single Secure Shell connection, firewall and router filters can be tightened to just one inbound port: the Secure Shell port (22).
VanDyke Software® VShell® server and SecureCRT® client enable Secure Shell tunneling on Windows, macOS, and Linux. Cross-platform tunneling is made possible by compliance to the SSH protocol. The full list of platforms supported by VShell and SecureCRT can be found in our System Requirements.
This paper shows how VanDyke VShell and SecureCRT provide a comprehensive, end-to-end solution to secure client/server applications. This paper:
- Examines threats addressed by tunneling over the public Internet or a company intranet
- Explains how Secure Shell port forwarding, authentication, and access control features work
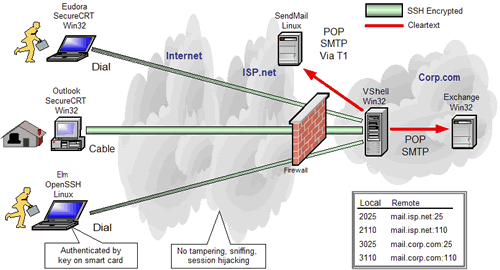
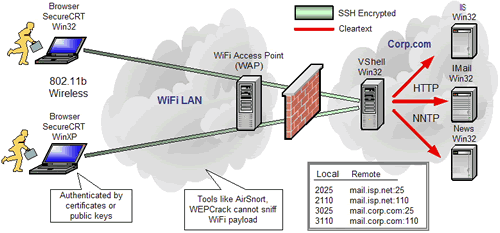
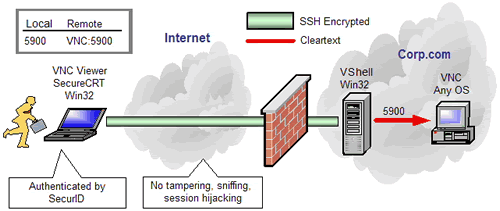
- Illustrates common applications like email, file sharing, and screen sharing as they are tunneled over residential broadband and WiFi networks
- Considers security implications and where tunneling is best used.
Note: IEEE 802.11 standards have changed since this article was written in 2006. However, the details regarding tunneling are still accurate.